Encryption algorithm commands are very important for many applications. For example, they make smart cards easier to use as encryption and decryption devices or for verifying digital signatures. Many smart card operating systems have their own set of commands that perform encryption algorithms. Because there is no such standard, smart card commands such as ENCRYPT, DECRYPT, SIGN DATA, and VERIFY SIGN Ì„ATURE appear. However, there are two commands that specifically handle encryption algorithms that are specified in the ISO/IEC 7816-8 standard.
Other encryption commands in the ISO/IEC 7816-8 standard are also mentioned in the following materials, as this is currently the only valid material for such commands, however, these standards have not been completed at the time of writing; their status For the committee draft CD (Committee Draft). This means that there may still be some minor modifications or even major changes before the final version.
The encryption-related functions in the ISO/IEC 7816-8 standard are decomposed between two commands. The MANAGE SECURITYENVIROMENT command allows various general conditions to be set before actually executing the encryption algorithm. This command transmits A "template" is given to the card, which contains relevant parameters. They remain effective For many applications, encryption algorithm commands are very important. For example, they make smart cards easier to use as encryption and decryption devices or to verify digital signatures. Many smart card operating systems have their own set of commands that perform encryption algorithms. Because there is no such standard, smart card commands such as ENCRYPT, DECRYPT, SIGN DATA, and VERIFY SIGN Ì„ATURE appear. However, there are two commands that specifically handle encryption algorithms that are specified in the ISO/IEC 7816-8 standard.
Other encryption commands in the ISO/IEC 7816-8 standard are also mentioned in the following materials, as this is currently the only valid material for such commands, however, these standards have not been completed at the time of writing; their status For the committee draft CD (Committee Draft). This means that there may still be some minor modifications or even major changes before the final version.
The encryption-related functions in the ISO/IEC 7816-8 standard are decomposed between two commands. The MANAGE SECURITYENVIROMENT command allows various general conditions to be set before actually executing the encryption algorithm. This command transmits A "template" is given to the card, which contains relevant parameters. They remain in effect until they are replaced by a new MANAGE SECURITY ENVIROMENT command. The template itself contains TLV-encoded data objects that allow for high variability in parameter transmission (and unfortunately its complexity).
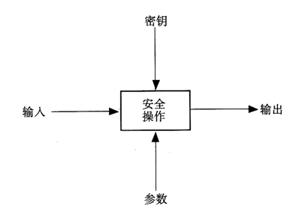
Figure 1 Commands for encryption in ISO/ICE 7816-8: The basic principles of MANAGE SECURITY ENVIRONMENT PERFORM ECURITY OPERATION
After all the options for the encryption function are set with the MANAGE SECURITY ENVIRONMENT command, the PERFORM SECURITY OPERATION command can be invoked, which allows a large number of security operations to be performed as long as they are supported by the smart card operating system. The number of possible options for this command is so great that not all support is mandatory. Although PERFORM SECURITY OPERATION is encoded with only one instruction byte, the eight different functions are distinguished by the parameter byte P1. The reason for this is that the number of command bytes left to encode the command is already quite tight at this point.
The functions of these two commands are shown in Tables 1 to 9. Figure 1 shows the basic principles of their operation.
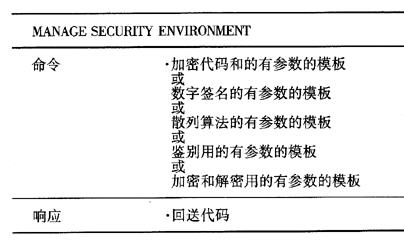
Table 1 Functions of MANAGE SECURITY ENVIRONMENT in accordance with ISO/IEC 7816-8
Since the PERFORM SECURITY OPERATION command is applied in many different ways, we will describe the functions separately according to different options below, without describing them in detail.
The PERFORM SECURITY OPERATION COMPUTE CRYPTOGRAPHIC CHECKSUM option is used to determine the Encrypted Checksum (CCS), which is commonly referred to as the MAC (Message Authentication Code). The padding used and the key are either implicitly given by the operating system or can be provided by the MANAGE SECURITY-ENVIRONMENT command. The option corresponding to this command is VERIFY CRYP-TOGRAPHIC CHECKSUM, which calculates the encrypted code of the transmitted data and compares it with the reference value also transmitted in the command. The result of this operation is met/not met and returned to the terminal.
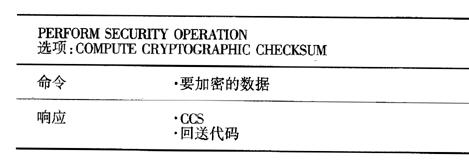
Table 2 PERFORM SECURITY OPERATION option COMPUTE CRYPTOGRAPHlC CHECKSUM according to ISO/IEC 78168

Table 3 Functions of VERIFY CRYPTOGRAPHIC CHECKSUM in accordance with PERFORM SECURITY OPERATION of ISO/IEC 7816-8
Two options, ENCIPHER and DECIPHER, provide pure encryption and decryption of the data, and the ENCIHER option is used to encrypt the data transmitted in the command. Depending on the options provided by the operating system, the MANAGE SECURITYENVIRONMENT command can be passed first to select the encryption algorithm used. Similarly, the mode to be used as the encryption algorithm must be set before the command is issued with the parameters passed. For the block encryption algorithm, it is still possible to choose between the ECB and CBC modes. Since the length of the array transferred to the card does not have to be exactly an integral multiple of the encryption algorithm block size, the padding method must be specified by a supplementary parameter, and equally important is the storage address of the key used by the algorithm in the smart card to encrypt the data.
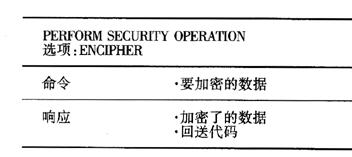
Table 4 Functions of ENCIPHER in accordance with PERFORM SECURITY OPERATION of ISO/IEC 7816-8
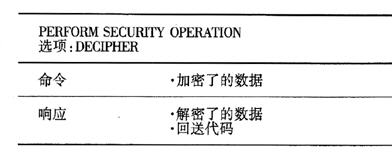
Table 5 Functions of DECIPHER in accordance with ISO/IEC 7816-8 PERFORM SEOURITY OPERATION
The inverse of ENCIPHER is DECIPHER, which allows the transmitted data to be decrypted in the same mode as used in ENCIPHER. Of course, the smart card must know the corresponding key, algorithm mode and padding mode. This information must be transmitted to the card's operating system using a MANAGE SECURITY ENVIRONMENT command.
Since the public key algorithm is introduced into smart card applications, this requires appropriate commands to use this new effective function. Smart cards are particularly suitable for signed applications because the secret key of the signed algorithm can be safely stored in memory and it cannot be read. The ISO/IEC 7816-8 standard describes four options for commands that can be used for digital signatures.
The HASH (hash) option of the PERFORM SECURITY OPERATION command can be used to calculate the hash value, the command either to transfer the data to be hashed, or to pass the calculated hash value outside the smart card and the data to be used in the last step. . In the latter case, the hash calculation for the last block is performed on the card. The advantage of this method is that the hash value can be formed significantly faster outside the card, but the last step is still in the card. From a purely cryptographic point of view, this provides only a small amount of additional security, but it can slightly limit the possibility of manipulating hash values ​​and is widely used in practice.
Since the amount of data hashed is usually greater than the maximum length of the data fields allowed in a command, a "Level-7" link is used in the 4.SH option, meaning that the arrays can be logically linked together at the application level. . The final hash array contains a flag to inform the command that the hash operation ends at this block.
This command option also has its own options, and the calculated hash value can either be immediately transmitted to the terminal in response to the command or stored in the card for subsequent commands. As described in the previous command, the padding and keys used are specified by a prior MANAGE SECURITY ENVIRONMENT command.
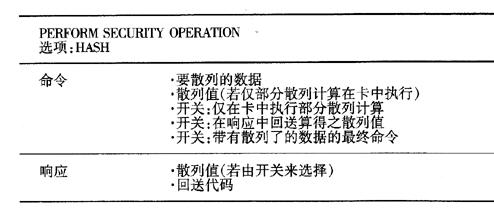
Table 6 Functions of the HASH option in accordance with PERFORM SECURTY OPERATION of ISO/IEC 7816-8
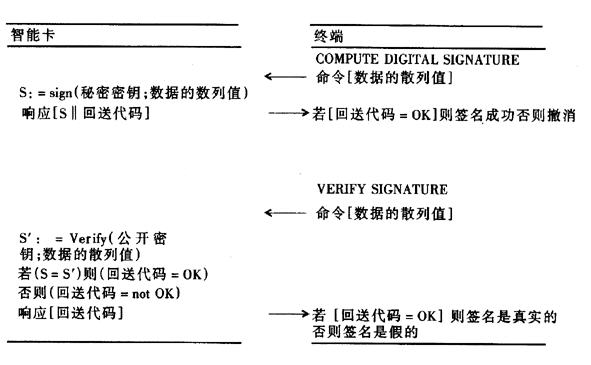
The COMPUTE DIGITAL SIGNATURE option can be used to sign data. The data string to be signed is usually already compressed into a hash value and must be passed to the smart card. Unless the previous one is the HASH option of the PERFORM SECURITY OPERATION command, the result already exists in the card. The COMPUTE DIGITAL SIGNATURE option also allows data to be signed to be transferred directly to the card. Hash the signatures before they are generated. For large amounts of data, a “level 7†hash can be taken with the HASH option.

Table 7 Functions of the COMPUTE DIGITAL SIGNATURE option in accordance with PERFORM SECURITY OPERATION of ISO/IEC 7816-8
If the length of the hash value does not correspond to the length of the input data of the public key algorithm, it must be filled. This option is also specified by the parameters in the MANAGE SECURITY ENVIRONMENT command, which is also used to determine the key used.
The ability to verify the COMPUTE DIGITAL SIGNATURE option is provided by the VERIFY DIGITAL SICNATURE option. In principle, any digital computer that is fast enough can be used to verify the signature because the required key is public. However, in many cases the validity of the public key must first be verified with an additional digital signature. This is really about security and should not be done on an insecure computer. For digital signature verification, the associated public key must either be implicitly known to the smart card or explicitly obtained by the command option VERIFY CERTIFICATE. The data to be verified can be passed directly to the VERIFY DIGITAL SIGNATURE or passed in the form of the associated hash value. All other parameters are the same as the COMPUTE DIGITAL SICNATURE option.

In an open system, the public key that verifies the digital signature is usually signed with the secret key of the credential authority. The reliability of the public key must be verified before use, as this is the only way to make sure that the key is not forged. This verification must be done in a secure environment, such as in a smart card, otherwise it may be subject to control. The VIIIIIIV CERTIÏ€CATE (Authentication Credentials) command option specifically provides verification of signed public keys. Once the public key is verified to be authentic, it can either be permanently stored on the smart card or immediately followed by a VERIFY DIGITAL SIGNATURE command.

If the operating system of the smart card supports the generation of an asymmetric encryption algorithm key pair, the process can be initiated by the ISO/IEC 7816-8 command GENERATE PUBLIC KEY PAIR. The specific functions are shown in Table 10. All parameters required for key generation must be set with the MANAGE SECURITY ENVIRONMEN command.
Figure 2 shows how the above described commands can be used to generate a digital signature and verification.
One Color Pad Printer//Usage and characters
- With sealed cup to protect environment , VOC volatilization reduced 86% and save ink over 25%.
- With coin aluminum structure ensure more stabilization and long life.
- Independent cylinder to drive sealed cup ensure removing ink completely. Make min Pressure to remove ink and prolong the life of sealed cup and steel plate;
- Both thick steel plates and thin steel plates installed , Choose according to customer requirements.
- Can print almost small size objects . So sold very nice in the world.
- Widely used in the industry field of cosmetics case, electron parts, Toys, plastics production, Housewares, gifts, decorations.
- Completely printing solution including ink and thinner , fixtures, steel plates, rubber pads provided when you send us samples;
Application fields
Electrons, hardware, autos, toys, gifts, Plastics, household appliances, artwork, stationery, adornment, cosmetic, commodity, sport goods, decorative lightings, woodwork, office supplies, Photo Materials, Kitchen utensils, Hotel supplies, Computer, Mobile, etc., industrial field.
One color pad printer //Advantage
- Using the dimensional modulating table, can be up and down, front, left, and rotation of the adjustment, which will help precise printing;
- T-slot structure, easy installation of fixtures and products;
- Hand pick and place workpiece, operating more handy;
- Microcomputer program control, the movement is more accurate and reliable;
- Test machine can be a single action adjustment, adjustment is completed, you can use the automatic mode of operation;
- Equipped with four counters, can effectively measure the number of products;
- Structure using die-casting aluminum, lightweight and solid.
- Independent Rubber pad up and down stroke and speed adjustment function;
- Sealed cup ink system, ink savings, and also to prevent the ink in the VOC emission into the air pollution of the environment, health protection of operating personnel;
- Sealed cup glide independent driving cylinder Blade pressure and Ink Removing Completely;
- Either use the tungsten steel ring, you can use a ceramic ring, and easy to replace;
- Temporary shutdown can prevent the ink to dry within the Sealed cup with INK function;
- World famous pneumatic components to ensure the long service life of machine;
- Rubber sliding shaft with hardened guide shaft grinding of high hardness, good abrasion resistance.
One Color Pad Printer
One Color Pad Printer,Semi Auto One Color Pad Printer,Electric One Color Pad Printer,Durable One Color Pad Printer
KC Printing Machine (Group) Limited , http://www.kcautopm.com